
Internet crime concept. Dangerous hacker, in hoodie shirt and dark red digital background around, stealing your data. Stock Photo by ©alexgeiger 147287155

320x568px | free download | HD wallpaper: hacker, red, sign, communication, illuminated, black background | Wallpaper Flare
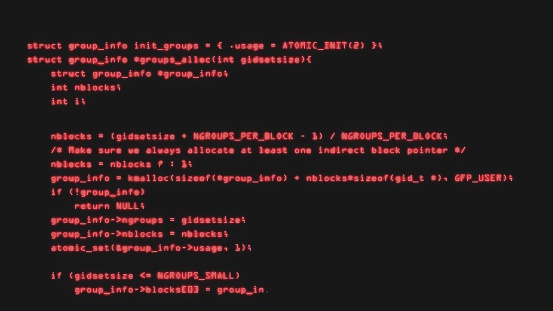
Red Computer Code Red Hacker Text Code On Screen Stock Photo - Download Image Now - Binary Code, Html, Internet - iStock

Hacker In A Grey Hoody Standing In Front Of A Red Datastream Background Of Binary Streams Cybersecurity Concept Stock Photo, Picture And Royalty Free Image. Image 63505383.
Computer hacking concept with faceless hooded male person using tablet, low key red and blue lit image and digital glitch effect Stock Photo - Alamy

Hacker In A Dark Red Hoody In Front Of A Digital Chinese Flag And Binary Streams Background Cybersecurity Concept Stock Photo, Picture And Royalty Free Image. Image 73793935.
Red Hacker Code on Screen Graphic Element Background Stock Video - Video of abstract, communication: 152420367













